Not ready for a demo?
Join us for a live product tour - available every Thursday at 8am PT/11 am ET
Schedule a demo
.svg)
No, I will lose this chance & potential revenue
x
x



At AppSecEngineer, one of our favourite things to do is find new ways for people to learn.
Back when we were learning application security, we had to deal with dull, one-dimensional training that sucked the joy out of the subject.
No one likes being stuck in a classroom while they watch kids outside in the playground.
That's why we're introducing the newest innovation to AppSecEngineer's amazing catalogue of courses: Security Playgrounds.
Security Playgrounds are a revolutionary new way to teach secure coding practices to developers.
They feature sandbox-style environments where you can learn new security skills and practice them in simulated environment.
Just like hands-on labs in our regular courses, the playgrounds are a way for you skip long video tutorials and get right into the action.
Step-by-step instructions tell you exactly what you need to do. Plus, they're all voice-assisted, which means you can listen to the instructions while you work.
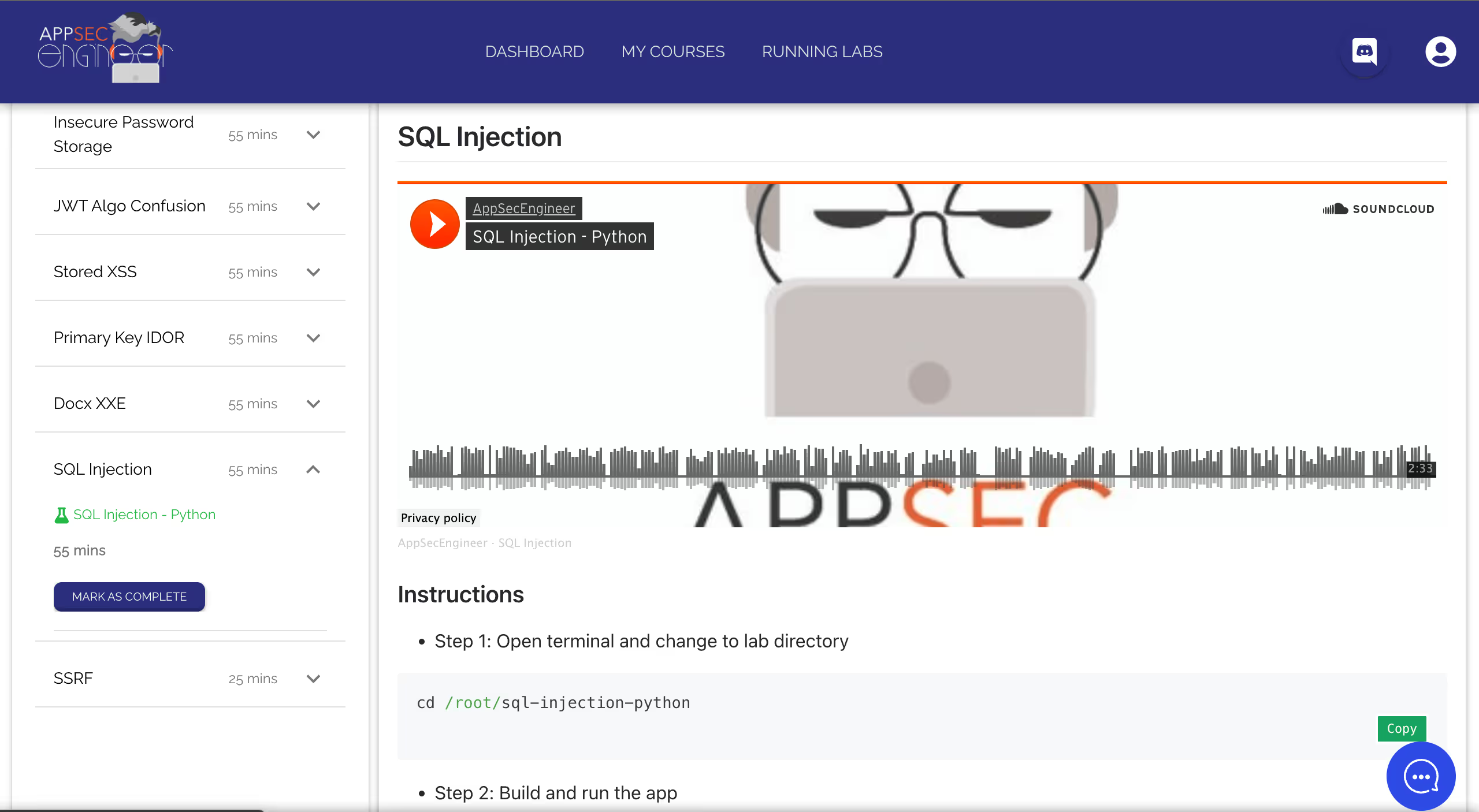
Most hands-on labs are part of our regular courses, which are aimed at security engineers, developers, architects, etc.
Our Security Playgrounds, on the other hand, are specifically geared towards developers.
Each playground is specifically built for developers who code in that particular language.
At the time of writing this article, we've released 3 playgrounds:
We have more playgrounds for Angular, Go, and .NET coming very soon!
If you're a developer who works in Python, you can start the Python Security Playground, which features 9 unique labs.
Each lab is built around a particular vulnerability, like Mass Assignment, Stored XSS, or SQL Injection.
These labs feature real-world security scenarios. You'll have access to the code, the build environment, and necessary tools like Docker, Nmap, Tplmap, etc.
All our playgrounds are attack-defence based. Your task in these playgrounds is to attack the build with that specific vulnerability, then secure it using what you've learned.
What's more, you can even change the code and play around with the scenarios to create new challenges for yourself.
Playgrounds are an incredibly easy way to teach security to developers in a way they'll intuitively understand.
Trying to use a scenario written in JavaScript to teach security to a Python developer wouldn't just be difficult, it's downright pointless.
Security skills in one language aren't transferable to another, and there's no 'one-size-fits-all' solution that could solve the problem for all developers.
Our playgrounds are built specifically for the language they're targeting, which means you won't have to waste time translating your learnings into a whole other language.
Skills you learn in a playground can apply to virtually any tech stack, as long as it's in the same language.
So while your skills are language-specific, they're not tied to any one kind of technology, and can be applied across cloud, containers, Kubernetes, etc.
One of our clients, a Fortune 500 company, needed personalised security training for developers working on multiple teams and in various languages.
Our Security Playgrounds gave them the assurance that once a programmer acquires the skills they need, they won't go obsolete even if the organisation changes their tech stack.
Read more: A Post-Pandemic Guide to Careers in Application Security
Playgrounds maybe specific to a computer language, but they're totally agnostic to human language.
One of the biggest problems with video lessons or online guides is that someone unfamiliar with English might have trouble understanding what's being taught.
Playgrounds, on the other hand, mostly rely on your hands-on knowledge of a programming language, which means non-English speakers don't have to struggle with the material.
You can change the code on your playground and play around with the environment. (Why else do you think we called it a playground?)
This means you can change up the security scenario and create new, interesting challenges for yourself without even changing browser tabs.
If you have an active AppSecEngineer subscription, you can try it right now! Just sign in to your account and find the playgrounds in the 'My Courses' section.
If you're still not sure about subscribing, why not get a free account? We don't ask for your credit card, and you can try out the hands-on labs from one of our 8 free courses.
So, what are you waiting for? Start your journey into AppSec today, and join our growing community on Discord to chat with folks just like you!



.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"
.svg)




.svg)



.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"


.svg)
.svg)




United States11166 Fairfax Boulevard, 500, Fairfax, VA 22030
APAC
68 Circular Road, #02-01, 049422, Singapore
For Support write to help@appsecengineer.com



.svg)
